Managing firewall rules are a tedious task but indispensable for a secure infrastructure. While all the cloud providers are having their own ACL and firewall rule offerings to protect your cloud resources.
Some of us are still using the firewall-d for instance/server-level security.
While firewall-cmd is really efficient to manage the firewall rules. Ansible can do the same thing a little better and clean.
In this article, we are going to see. How to manage your CentOS or Linux firewall firewall-d rules with Ansible firewallD module
Ansible FirewallD Examples
Here we list few examples of the Ansible FirewallD module to manage the services and ports.
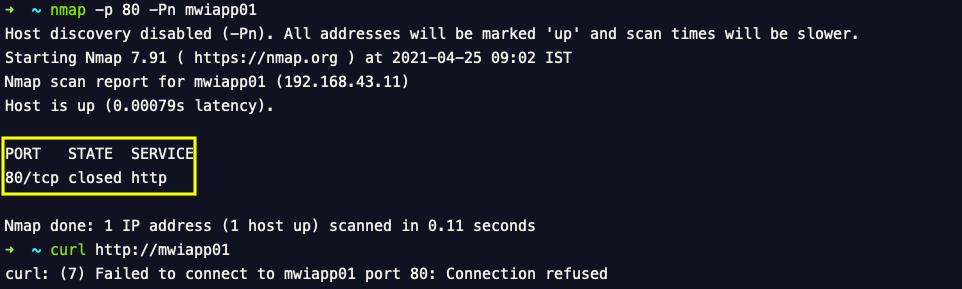
Validate if the HTTP/HTTPS service is Open or blocked
You can use a command nmap to see if the port is blocked or open, If you see the state as closed which means it is blocked by firewalld
Now let us enable HTTP and HTTPS services that would open the port 80 and 443
Enabling HTTP and HTTPS Service
Here is the Ansible playbook with firewallD module to enable HTTP and HTTPS service that inturns open up port 80 and 443
This playbook is designed to run on the localhost and can be chagned to run remote by removing the
connection: localand updatinghostsparameter
---
- name: FirewallD
hosts: localhost
connection: local
tasks:
- name: FirewallD rules
firewalld:
permanent: yes
immediate: yes
service: "{{ item }}"
state: enabled
with_items:
- http
- https
In this playbook, we are using with_items for loop processing and enabling multiple services in a single task.
immediate: yes flag would make sure that the firewall rules are implemented immediately.
Execution Output
[root@MWINODE01 vagrant]# ansible-playbook firewalld.yml [WARNING]: provided hosts list is empty, only localhost is available. Note that the implicit localhost does not match 'all' PLAY [FirewallD] *************************************************************** TASK [Gathering Facts] ********************************************************* ok: [localhost] TASK [FirewallD rules] ********************************************************* changed: [localhost] => (item=http) changed: [localhost] => (item=https) PLAY RECAP ********************************************************************* localhost : ok=2 changed=1 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
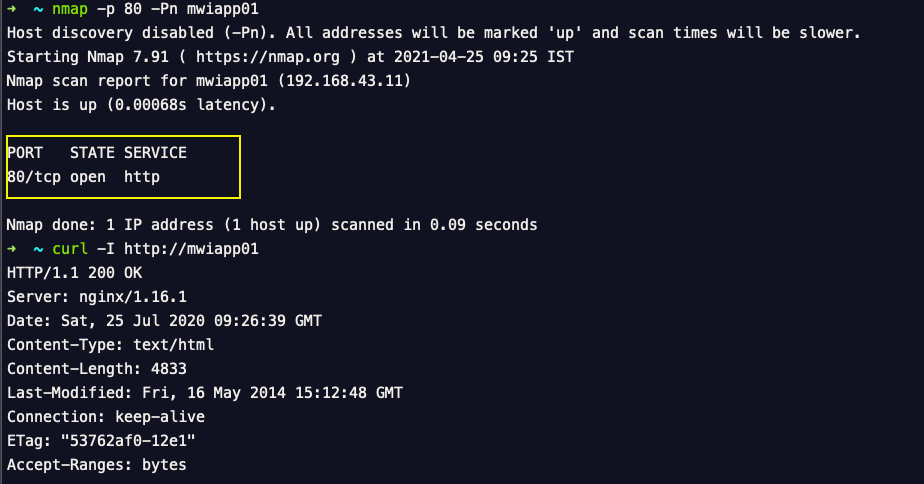
Let us Validate if the HTTP/HTTPS services are Open
Now you can rerun the nmap and curl command to validate if the HTTP/HTTPS services are open and enabled.
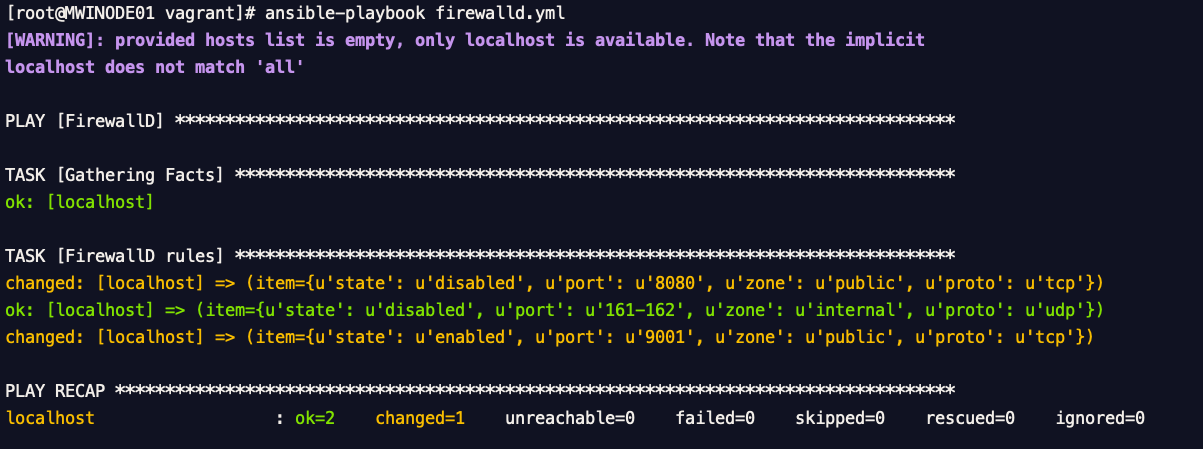
Enabling & Disabling Multiple Ports on different Zones
Here is the Generic playbook which can help you enable and disable, various different ports on different zones.
This simple playbook can be used for managing entire host firewall rules at once.
---
- name: FirewallD
hosts: localhost
connection: local
tasks:
- name: FirewallD rules
firewalld:
permanent: yes
immediate: yes
port: "{{item.port}}/{{item.proto}}"
state: "{{item.state}}"
zone: "{{item.zone}}"
with_items:
- {port: "8080", proto: "tcp", state: "disabled", zone: "public" }
- {port: "161-162", proto: "udp", state: "disabled", zone: "internal" }
- {port: "9001", proto: "tcp", state: "enabled", zone: "public" }
Playbook result
Using Rich Rule with Ansible FirewallD
You can use Rich rules with the Ansible FirewallD module.
Here is the Example playbook with the Rich rule to accept ftp and drop http for one minute along with the audit log
---
- name: FirewallD
hosts: localhost
connection: local
tasks:
- name: FirewallD rules
firewalld:
permanent: yes
immediate: yes
rich_rule: "{{ item }}"
state: enabled
with_items:
- 'rule service name="ftp" audit limit value="1/m" accept'
- 'rule service name="http" audit limit value="1/m" drop'
Execution Result
[root@MWINODE01 vagrant]# ansible-playbook firewalld.yml [WARNING]: provided hosts list is empty, only localhost is available. Note that the implicit localhost does not match 'all' PLAY [FirewallD] ***************************************************************************************************** TASK [Gathering Facts] *********************************************************************************************** ok: [localhost] TASK [FirewallD rules] *********************************************************************************************** changed: [localhost] => (item=rule service name="ftp" audit limit value="1/m" accept) changed: [localhost] => (item=rule service name="http" audit limit value="1/m" drop) PLAY RECAP *********************************************************************************************************** localhost : ok=2 changed=1 unreachable=0 failed=0 skipped=0 rescued=0 ignored=0
Creating Port Redirection using Ansible Firewall Rich Rule
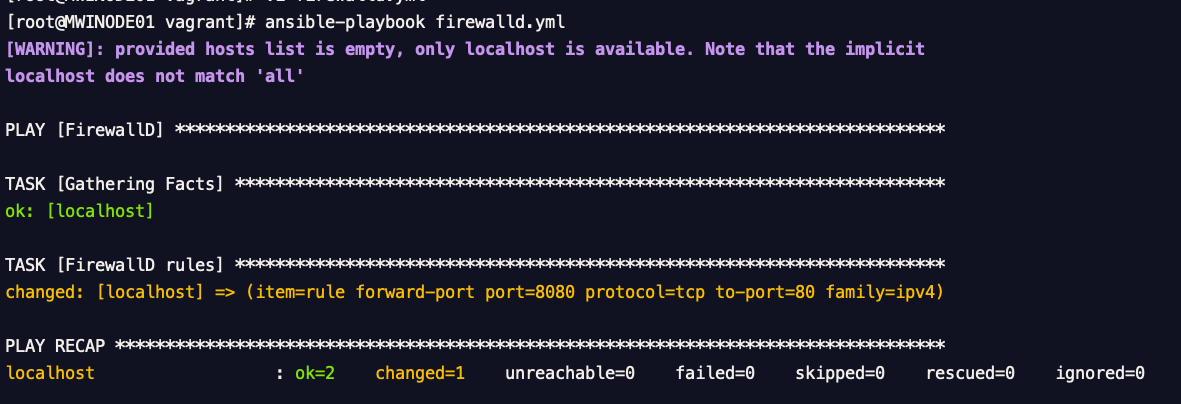
Here is the ansible-playbook example to setup Port Forwarding or Port redirection with Ansible FirewallD module
In this task, we are going to set up a port forwarding from port 8080 to port 80 and serve the static page from Nginx
---
- name: FirewallD
hosts: localhost
connection: local
tasks:
- name: FirewallD rules
firewalld:
permanent: yes
immediate: yes
rich_rule: "{{ item }}"
state: enabled
with_items:
- 'rule forward-port port=8080 protocol=tcp to-port=80 family=ipv4'
Here is the execution result
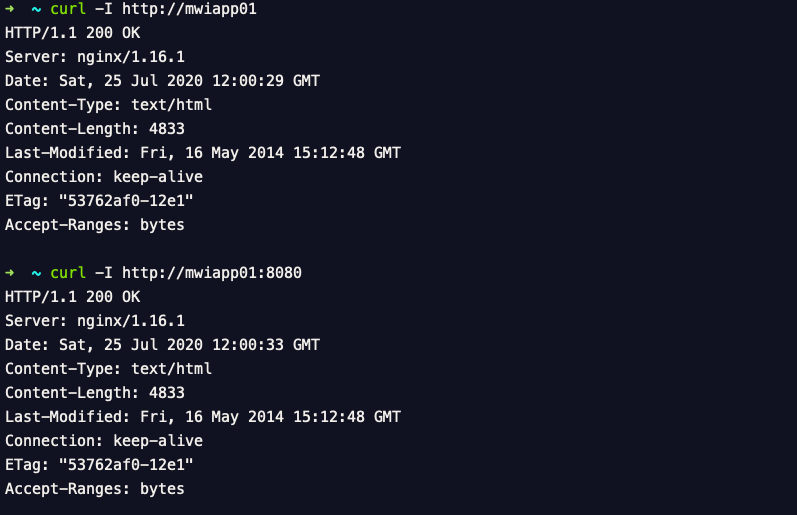
Let us quickly validate the port forwarding by accessing the website on port 8080 and 80
Conclusion
Ansible FirewallD module can help you efficiently manage your firewall rules with more control and idempotent.
Rich rules are better executed and managed with Ansible FirewallD module. The only key feature I find it missing was listing and reading the already available rules.
For which we have to still rely on the firewall-cmd command line.
Hope this article helps and if you have any better examples. please let us know on the comments section
Cheers
Sarav AK

Follow me on Linkedin My Profile Follow DevopsJunction onFacebook orTwitter For more practical videos and tutorials. Subscribe to our channel
Signup for Exclusive "Subscriber-only" Content