Let's suppose your AWS infrastructure is under DDOS attack and your Load balancers and Applications are flooded with requests.
The Immediate action you can take is to block the IP you have identified.
If you have monitoring tools and Log management tools like Datadog, EFK, Splunk etc. they can be used to get the IP address of the spammer or the bot. or Simple NGINX/Apache log can do.
Even the monitoring systems have auto threat detection or anomaly detection to identify this prior.
If you are not having such monitoring systems in place. I would recommend enabling WAF your application load balancer which can apply rate limit and block the IP.
But in this article, we are going to show you how you can block a particular IP or list of IPs from accessing your infrastructure.
While talking about infrastructure, It includes all the Application Load Balancers, network load balancers etc. So if you want an IP to be blocked from accessing all your applications this could help you.
Steps to Block IP in AWS VPC ( Global Level)
- Go to
VPCservices section and find your VPC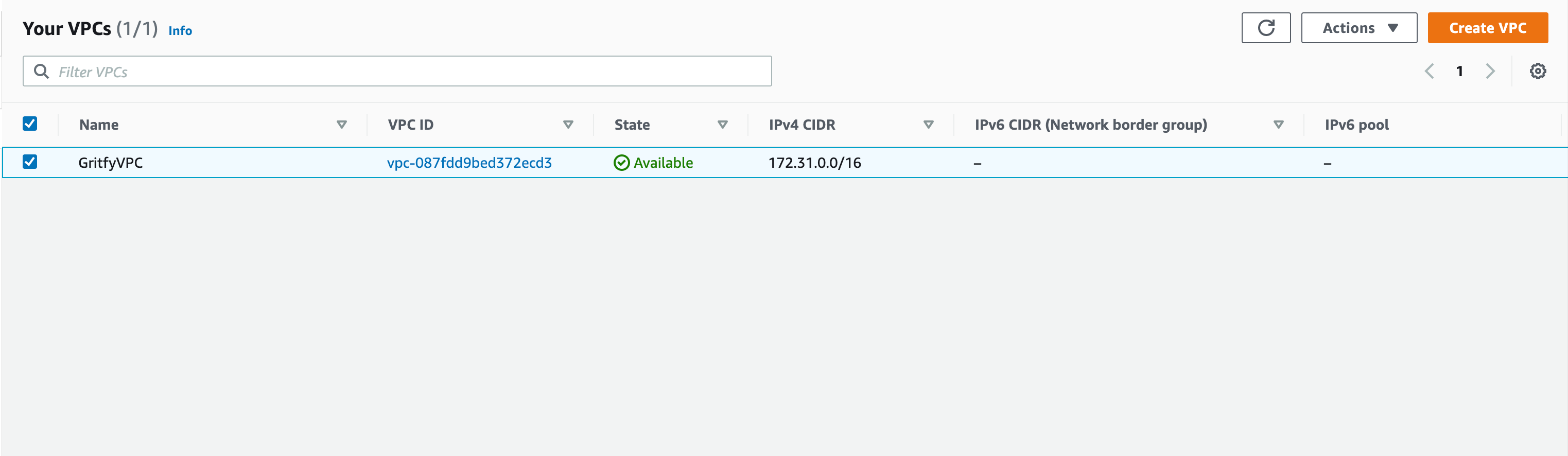
- Click on the VPC go into the Details page and find the primary
NACLNetwork Access Control List of the VPC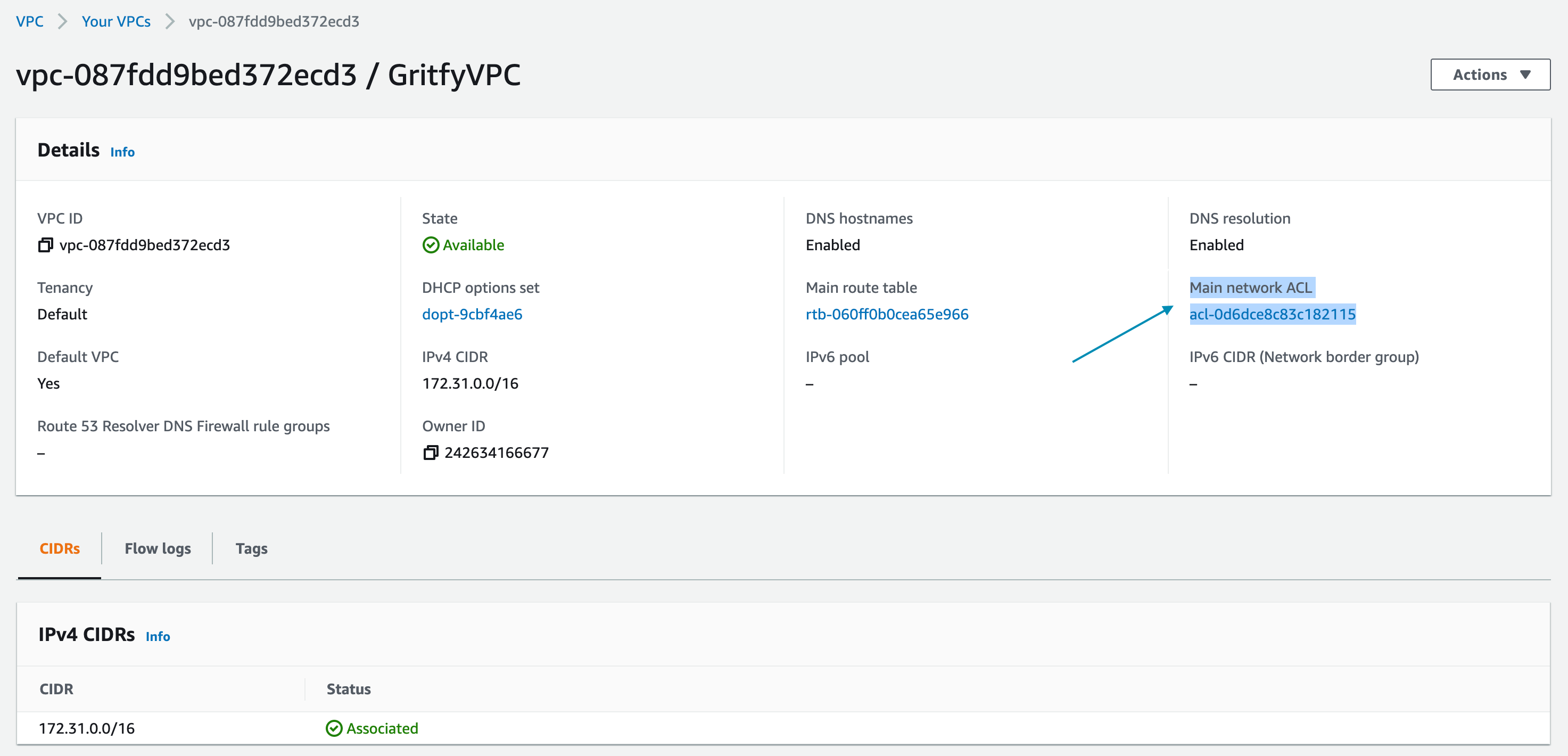
- Click on the NACL ID hyperlink and go to the NACL Inbound rules tab
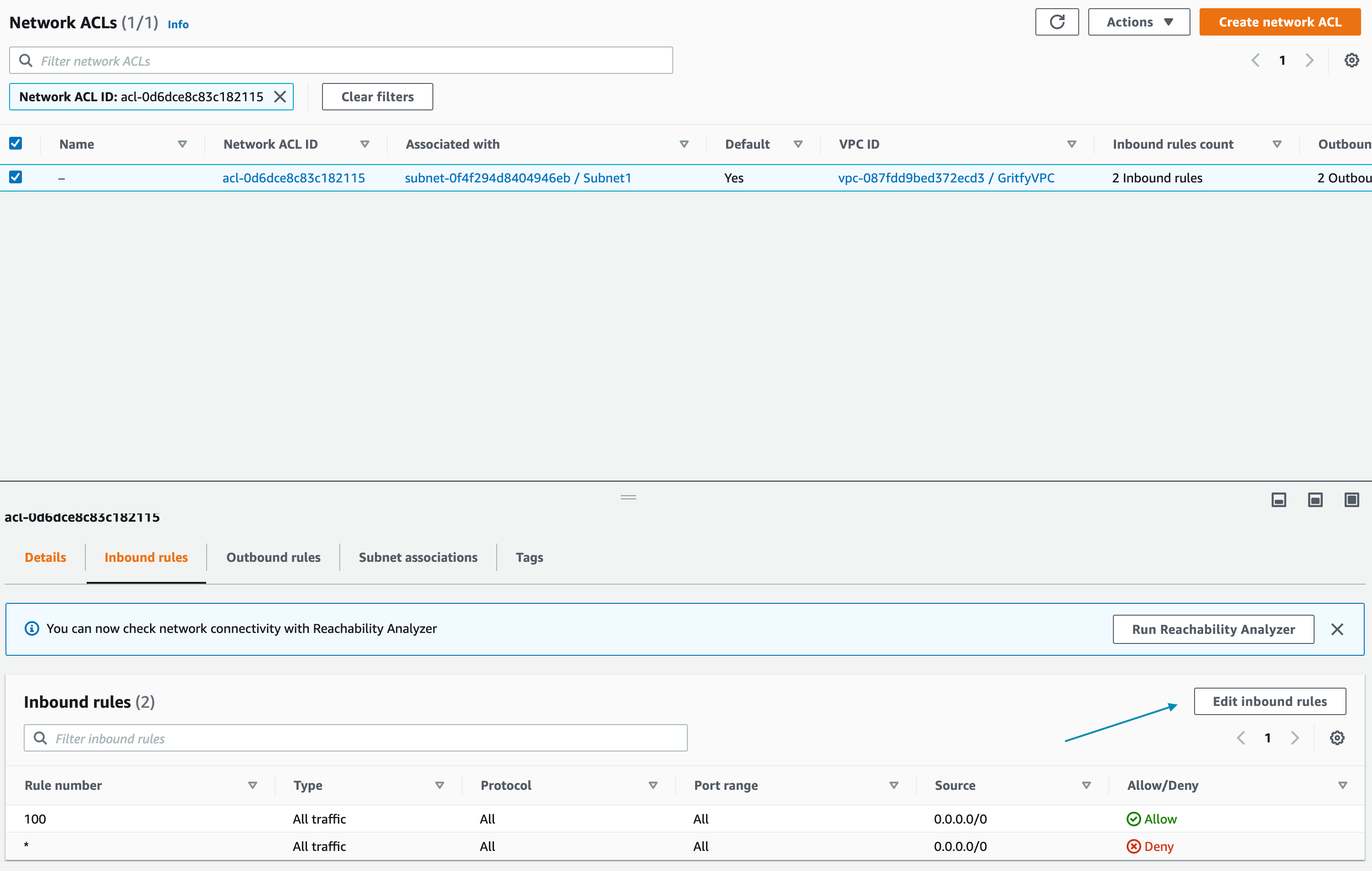
- Click on the Edit Inbound Rules button
- On the Edit Inbound Rules page. Click on the Add new rule button
- Give Rule number lower than the
All traffic - Allowthe rule which defaults to100you can give1or lower than 100 and work your way upwards upon every single IP you are blocking - Choose the Type from the drop down. Select All Traffic to block all the traffic from the IP
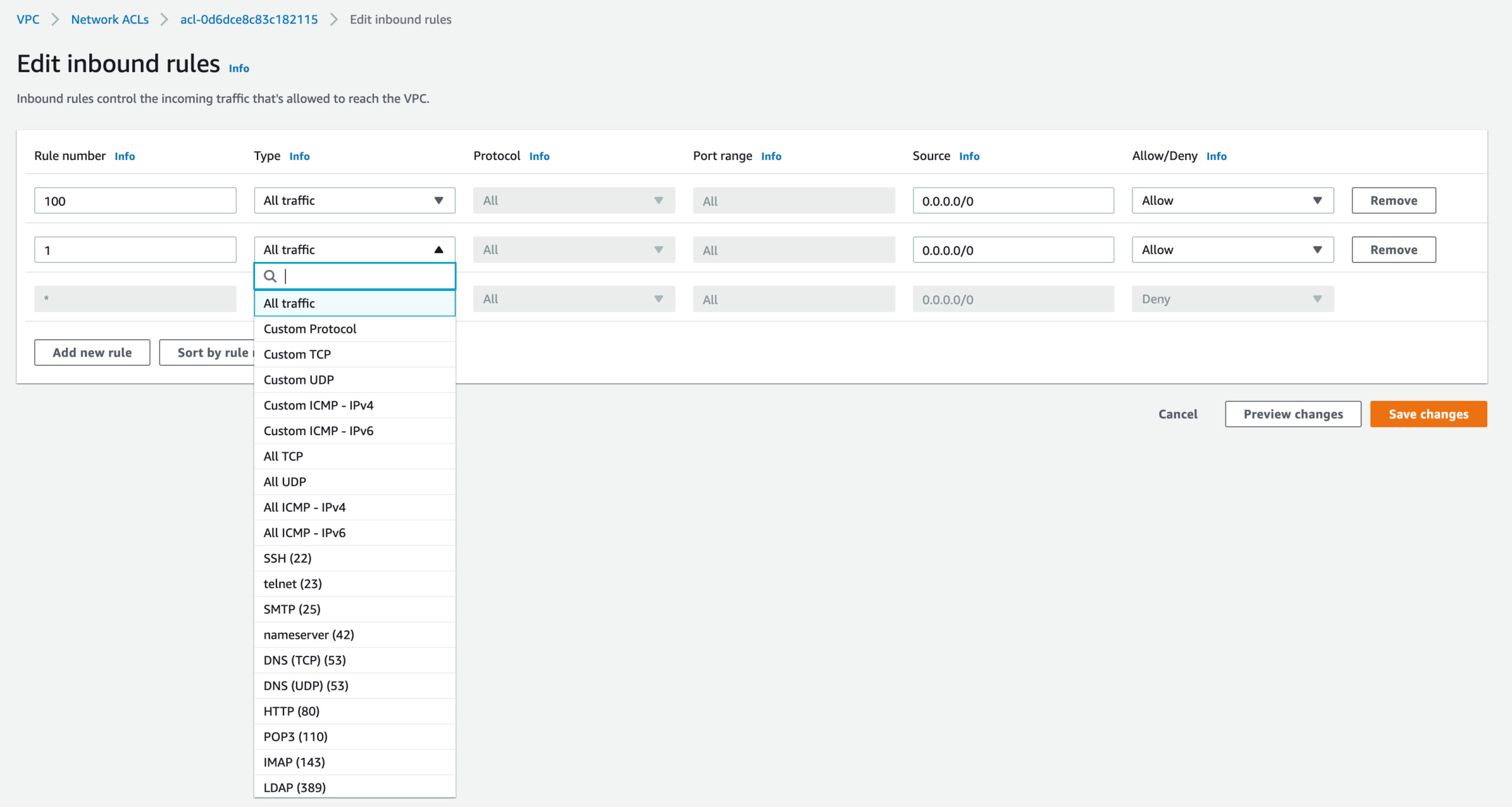
- Enter the Port Range you would like to block. Choose
Allfor all the ports ( If you have chosen All traffic this is not needed) - Enter the Source IP CIDR range if single IP add
/32at the end - Select Deny to deny the requests coming from the IP matching the port tange.
- Click on the Sort by rule number to validate that the default rule 100 is staying at the bottom
- Save the changes by clicking on Save Changes
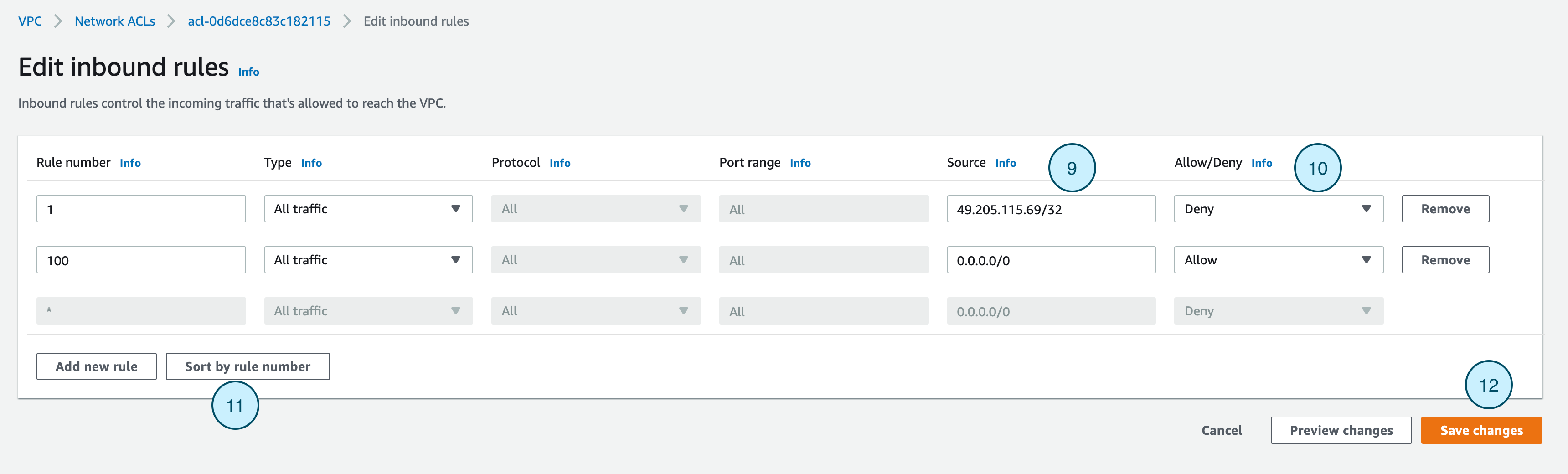
This is how you can block an IP address Global level of your overall infrastructure.
How to block IP at the ALB level or Server Level
If you do not want to block the IP from your entire Infra but to block only to certain application
You have a few options
- Create rules in Application Load Balancer to Deny the IP
- Create a WAF policy that matches the Source IP and block
- EC2 Security group level blocking with help of Security groups
- Within the EC2 instance (Ubuntu/Linux) use
firewallDto block the IP
Create rules in Application Load Balancer to Deny the IP
Another famous way to block the traffic at Application Load Balancer is to do it through ALB Rules.
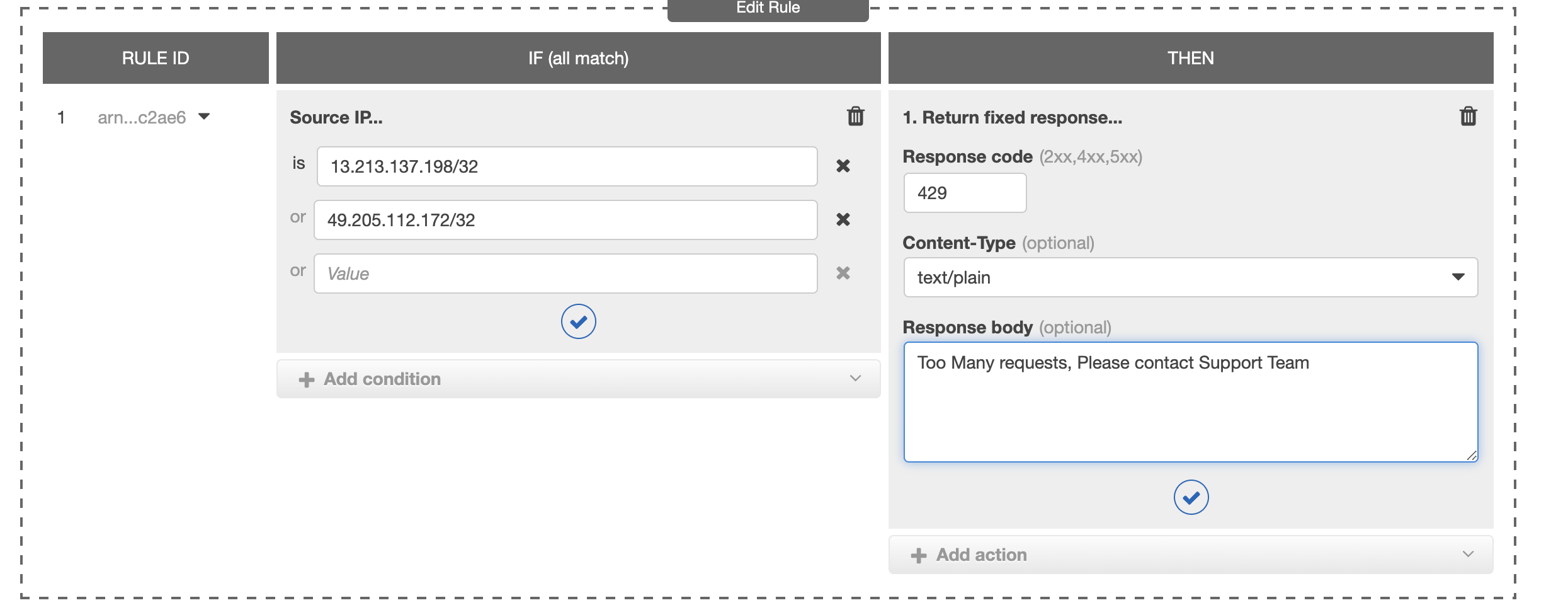
You can create a rule like shown below and return some custom response if the IP matches the IP you want to block.
here is a screenshot of some sample rule for your reference
If the Source IP is X or Y you can return a fixed response like HTTP 429 with some custom response body like this Too many requests from this ip etc.
This is one more efficient way of blocking IP at the Elastic Load Balancer Level.
Remember, This can be done only at the Application and network load balancer as Classic Load Balancer does not support the rules for processing.
Hope this article was helpful to you.
let us know in case of any queries or feedback on the comments
Cheers
Sarav AK

Follow me on Linkedin My Profile Follow DevopsJunction onFacebook orTwitter For more practical videos and tutorials. Subscribe to our channel
Signup for Exclusive "Subscriber-only" Content