Some Background
When it comes to handling the web application related vulnerabilities. Most of the vulnerabilities could be fixed by having the proper configuration at the F5 level.
By using the right configuration at the F5. like having proper SSL Cipher at the SSL profile of the VIP (or) creating and mapping specific irules to remove (or) modify some of the critical cookies like JSESSIONID (or) BigIpServer and mark them secure and HTTP only or enabling/inserting "Strict Transport Security" headers etc.
this post is just to share the iRule which helps to mark the cookie as secure and httponly
Why should we do it?
As a summary we are giving the reason why should we do it?
Reason for marking them httponly
When you tag a cookie with the HttpOnly flag, it tells the browser that this particular cookie should only be accessed by the server. Any attempt to access the cookie from client script is strictly forbidden. Thereby, we make it hard for the attacker to execute the XSS cross site scripting attack.
Reason for marking them as secure
In general when the site is available through HTTP and HTTPS both. There are chances that the attacker can tamper/hack the authentication related cookies from the HTTP request made by someone to the server and use the same cookies over HTTP/HTTPS to run the exploit (or) even pretend to be the user(victim) to the server and do evil.
If you mark sensitive and confidential cookies like SSO cookies or authentication related cookies with a secure flag, the marked cookies will only be sent over an HTTPS connection. Thereby, we can make it hard for the attacker to hack into your account (like net banking)
The iRule to mark the cookies as secure and httponly
when HTTP_RESPONSE { set Cookies [HTTP::cookie names] # Loop though cookies foreach mycookie $Cookies { if { ( $mycookie starts_with "JSESSIONID" or $mycookie starts_with "BIGipServer" ) } { # Reinsert cookie with version 1 then mark httponly if { [HTTP::cookie version $mycookie] != 1 } { set ckval [HTTP::cookie value $mycookie] set ckpath [HTTP::cookie path $mycookie] HTTP::cookie remove $mycookie HTTP::cookie insert name $mycookie value $ckval path $ckpath version 1 } # Mark Cookie httponly HTTP::cookie httponly $mycookie enable # Mark F5 Cookies as secure HTTP::cookie secure $mycookie enable } } }
Some Explanation
We get all the cookies from the response and trying to find the cookies starts with either JSESSIONID and BIGipServer using starts_with module of F5 Big IP iRule and adding a version attribute to them to prevent redoing the same work (or) duplicating the efforts.
Once the version attribute has been added. we mark these cookies as httponly and secure The following lines do that.
# Mark Cookie httponly HTTP::cookie httponly $mycookie enable # Mark F5 Cookies as secure HTTP::cookie secure $mycookie enable
How to Verify
The process given below is for chrome.
Hit the Corresponding URL (VIP) in your browser -> open Developer tools -> Go to Networks tab -> Retry the URL -> click on the main page (or) domain name you have requested in the Name column amongst various pages served (css/images etc)
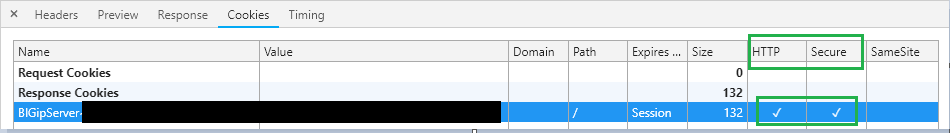
Now, Go to the Cookies tab
you can find the BigIPServer Cookie and make sure that HTTP and Secure attributes are checked.
In chrome, it looks like this.
Note*: we have intentionally covered/hidden some portion of Name and the Value for security reasons
Hope this helps.
Leave a ratings if you like [ratings]
Thanks
SaravAK

Follow me on Linkedin My Profile Follow DevopsJunction onFacebook orTwitter For more practical videos and tutorials. Subscribe to our channel
Signup for Exclusive "Subscriber-only" Content