Overview
Vulnerability in the Oracle WebLogic Server component of Oracle Fusion Middleware (subcomponent: WLS Core Components). Supported versions that are affected are 10.3.6.0, 12.1.3.0, 12.2.1.2 and 12.2.1.3. Easily exploitable vulnerability allows unauthenticated attacker with network access via T3 to compromise Oracle WebLogic Server via unsafe deserialization of Java objects. Successful attacks of this vulnerability can result in takeover of Oracle WebLogic Server.
In a vulnerable system, WebLogic administrators can identify possible Java deserialization attacks if similar exceptions are seen in their WebLogic logs:
To exploit the CVE-2018-2628 vulnerability, the first step is to establish a socket connection with the T3 service available on the service port of WebLogic Server. Therefore, the attack can be blocked by controlling access to the T3 protocol. WebLogic Server provides a default connection filter called weblogic.security.net.ConnectionFilterImpl. This filter accepts all inbound connections. It is advisable to configure a rule through this filter to control access to T3 and T3S protocols.
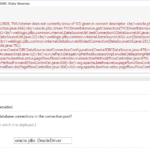
Connection filter from Weblogic Console
- Access the administration console of WebLogic Server.
- Click Base_domain in the left pane and then click the Security and Filter tabs successively to open the filter configuration page.
- Type security.net.ConnectionFilterImplin the Connection Filter field and * * 7001 deny t3 t3s in the Connection Filter Rules field.
Note : Protocols specifies the protocols to be filtered. (The value must be http, https, t3, t3s, iiop, iiops, and/or ftp.) If no protocol is specified, all protocols will be filtered.
- Click Save. Then this rule takes effect immediately without needing a restart.
Connection filter through Weblogic Server command line
- Access the WebLogic Server through command line Go to basefolder/weblogic/version-directory/user-projects/base-domain/config.
- Vi Config.xml and update for weblogic connection filter lines as below nodemanager line.
<connection-filter>weblogic.security.net.ConnectionFilterImpl</connection-filter>
<connection-filter-rule>10.1.xx.xx 10.1.xx.xx 7001 deny http</connection-filter-rule>
<connection-logger-enabled>true</connection-logger-enabled>
Note : Protocols specifies the protocols to be filtered. (The value must be http, https, t3, t3s, iiop, iiops, and/or ftp.) If no protocol is specified, all protocols will be filtered.
- Click Save. Then this rule takes effect immediately without needing a restart . but restarting domain is recommended.
More from Middleware Inventory
Oracle Weblogic Basic AuthenticationOverview Oracle WebLogic Server authentication is enabled by default. However, this configuration prevents Oracle WebLogic Server from using application managed authentication. You must disable Oracle WebLogic Server authentication by setting the enforce-valid-basic-auth-credentials parameter to false. Procedure To disable Oracle WebLogic Server authentication: In a text editor, open the xmlfile from the domain folder. The config.xml file is in the Oracle/Middleware/user_projects/domains/domain_name/config directory. Locate the <security-configuration> Add the…
-
Weblogic 12c Oracle Datasource TNS ExceptionProblem While creating a Oracle Data source in weblogic 12c, If you are encountering the below error message upon TestConnection. Though all the SID(Database name) and Host and Port are Correct Listener refused the connection with the following error: ORA-12505, TNS:listener does not currently know of SID given in connect descriptor…
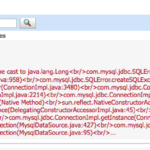
Weblogic - Datasource exception java.lang.ClassCastException: java.math.BigIntegerThis post is to discuss about a particular Issue we often face in weblogic 12c and how to resolve the same The Issue While trying to create mysql Datasource in weblogic, the following exception occurs and unable Test Connection (or) Test Configuration fails. java.lang.ClassCastException: java.math.BigInteger cannot be cast to java.lang.Long<br/>com.mysql.jdbc.SQLError.createSQLException(SQLError.java:1058)<br/>com.mysql.jdbc.SQLError.createSQLException(SQLError.java:972)<br/>com.mysql.jdbc.SQLError.createSQLException(SQLError.java:958)<br/>com.mysql.jdbc.SQLError.createSQLException(SQLError.java:903)<br/>com.mysql.jdbc.ConnectionImpl.buildCollationMapping(ConnectionImpl.java:1025)<br/>com.mysql.jdbc.ConnectionImpl.initializePropsFromServer(ConnectionImpl.java:3480)<br/>com.mysql.jdbc.ConnectionImpl.connectOneTryOnly(ConnectionImpl.java:2444)<br/>com.mysql.jdbc.ConnectionImpl.createNewIO(ConnectionImpl.java:2214)<br/>com.mysql.jdbc.ConnectionImpl.<init>(ConnectionImpl.java:797)<br/>com.mysql.jdbc.JDBC4Connection.<init>(JDBC4Connection.java:31)<br/>sun.reflect.NativeConstructorAccessorImpl.newInstance0(Native…
-
What is ORACLE_HOME,MW_HOME,WL_HOME in Weblogic 12cThe Objective In this post, we are going to see what are the different types of home directories available in weblogic and the various options or methods to find the ORACLE_HOME, MW_HOME and WL_HOME of your weblogic 12c installation. The commands and the methods are mostly given for the LINUX…
-
Docker Weblogic : Run Oracle Weblogic 12c on DockerThe Introduction to Docker Weblogic In this post, we are going to be exploring the quick and easy option available to get started with weblogic and Docker. In this post, we are going to see how to create a weblogic container in docker in a few easy steps. The post's…